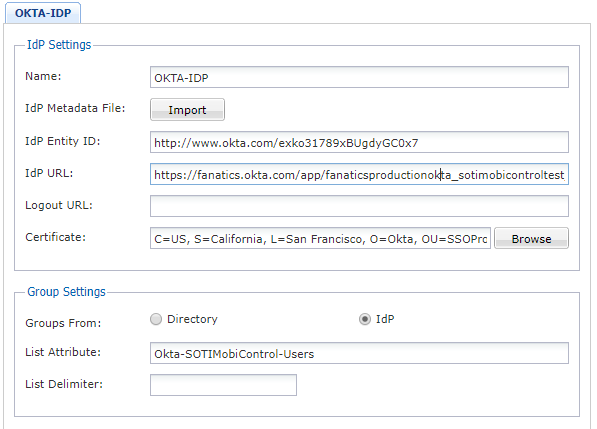
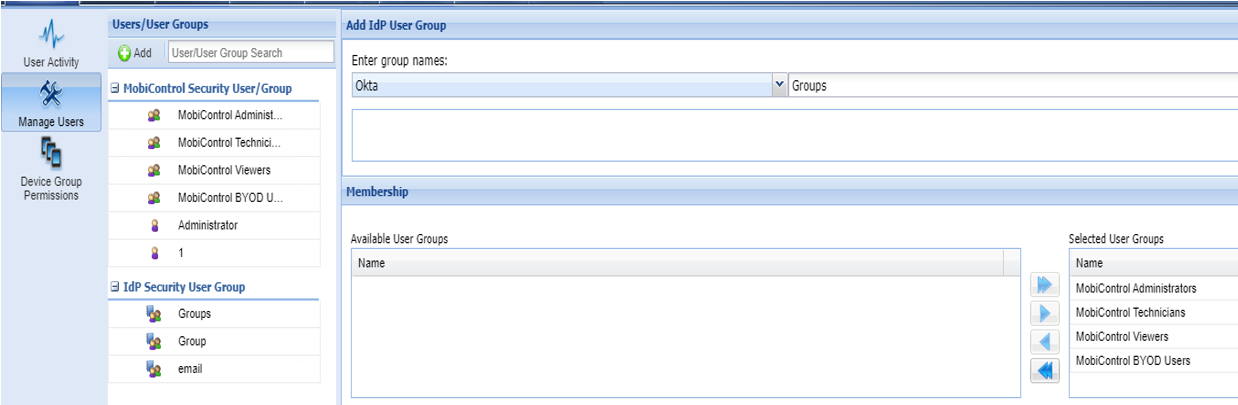
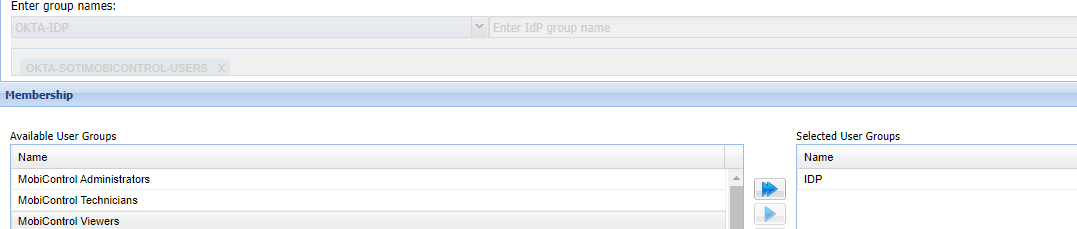
Attempting to setup SSO to work with OKTA however I was running into an issue in which we receive the following error
HTTP/1.1 405 Method Not Allowed
Content-Length: 1665
Content-Type: text/html
Server: Microsoft-HTTPAPI/2.0
X-Frame-Options: SAMEORIGIN
X-Content-Type-Options: NOSNIFF
The data was initially imported with eh metadata file and the one thing that threw me off was the list attribute which I want sure what would be required for the field. I wasn't sure if that was the root cause but figured I would reach out here to see if anyone else had this before.