Hi,
I am having an issue where when a Samsung tablet restarts (Enterprise Work Managed, Android Version 11 to 13) it shows lock screen and until someone actually unlocks device, the device is not seen by MobiControl. It's like MobiControl agent only runs when the screen is unlocked the first time.
I tried to disable lockscreen in Authentication Profile, but it did not make a difference, the lock screen persist.
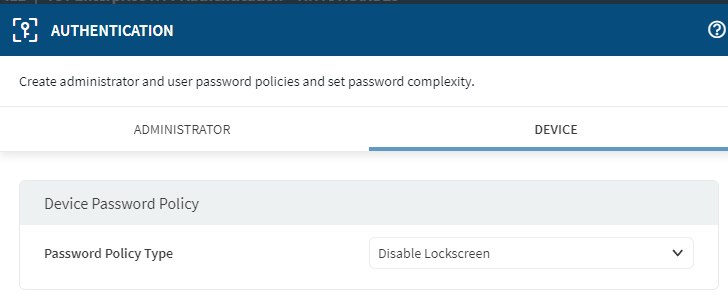
This causes a problem in that I lose access/control of the device unless someone logs them in. Device reboot sometimes when they get an update from Know E-Fota.
if MobiControl is an admin for the device, why doesn't it load at startup? I confirmed MobiControl is a device admin.
I tried OEMCONFIG through the Samsung plugin but it didn't have anything to set/disable the lock screen.
Any thoughts or ideas?
Thanks,