Hello Everyone,
currently i am struggling with the work profile on android.
First some infos about MC and MC Agent:
MC Version: 14.4.4.1045 (cloud hosted by SOTI)
MC Agent: 14.1.5 Build 1059 (Android Enterprise Agent from GoogePlay)
So we are using Samsung S10 devices. They are up to date with firmware/security updates.
The devices are configured as "Managed Work Profile" in MobiControl. Everything works fine except one thing.
After i enrolled the devices into MC i am no longer able to install any Apps via apk's out of my work profile (container).
They don't have any profiles assigned which could disable the installation from unknown sources.
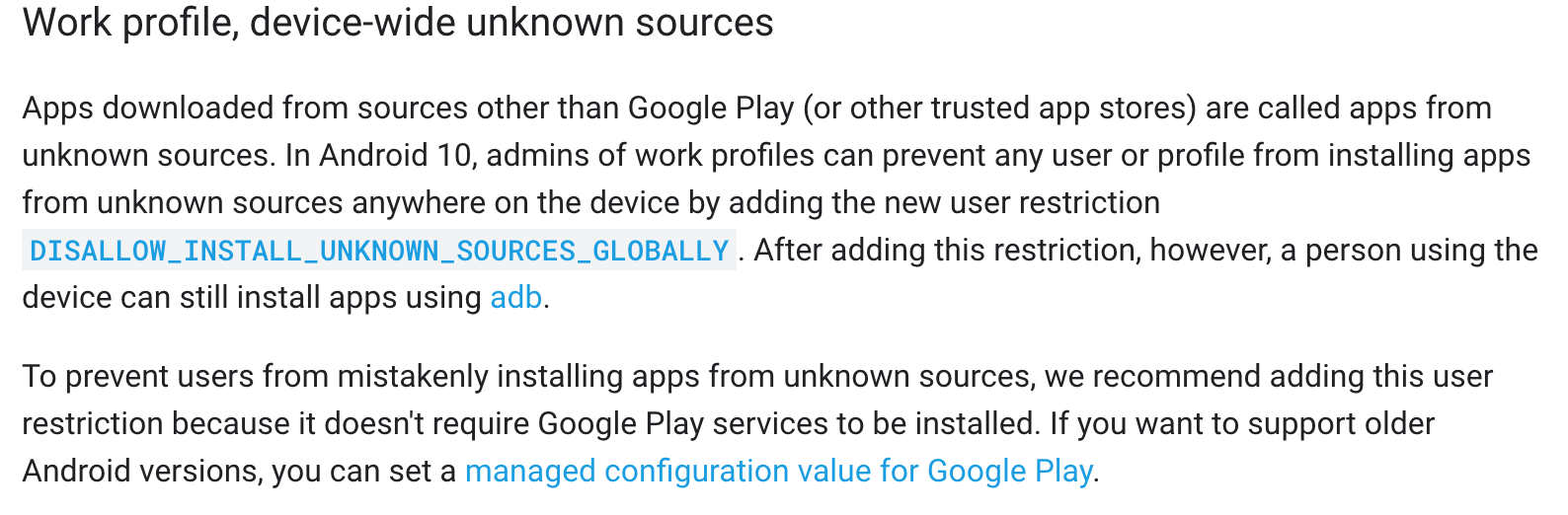
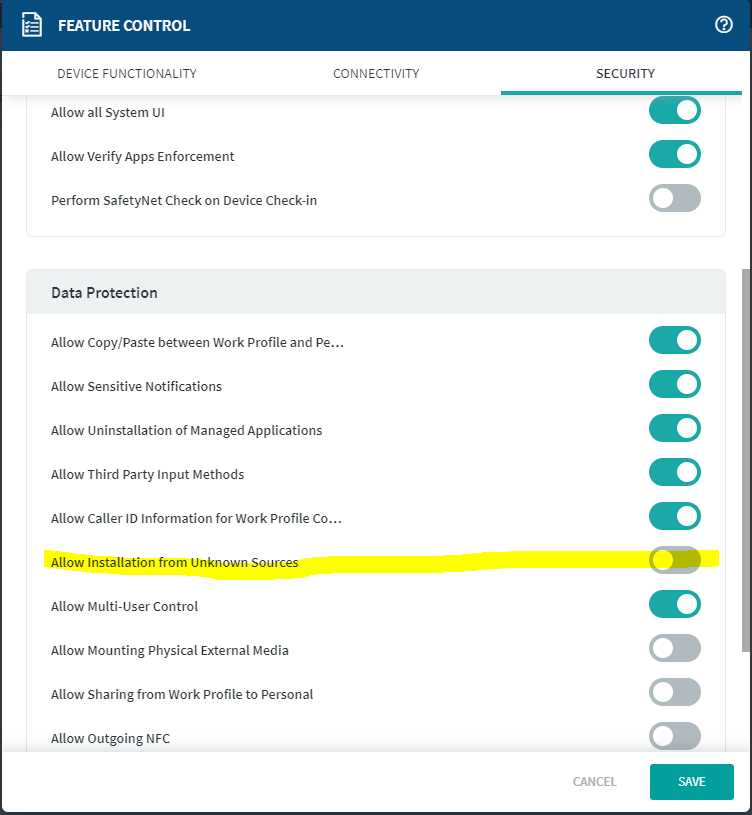
In the feature control i am able to allow the installation from unknown sources. But this count only for Fully Managed devices
and not Managed Profile devices.
So does it mean i am not allowed to install any apks at all because there could be an app
who could "attack" the work profile?
Is there still a way to allow the installation? Or am i doomed? Cause my useres should be allowed to install anything they
want. It is up in their responsibility when they do something wrong.