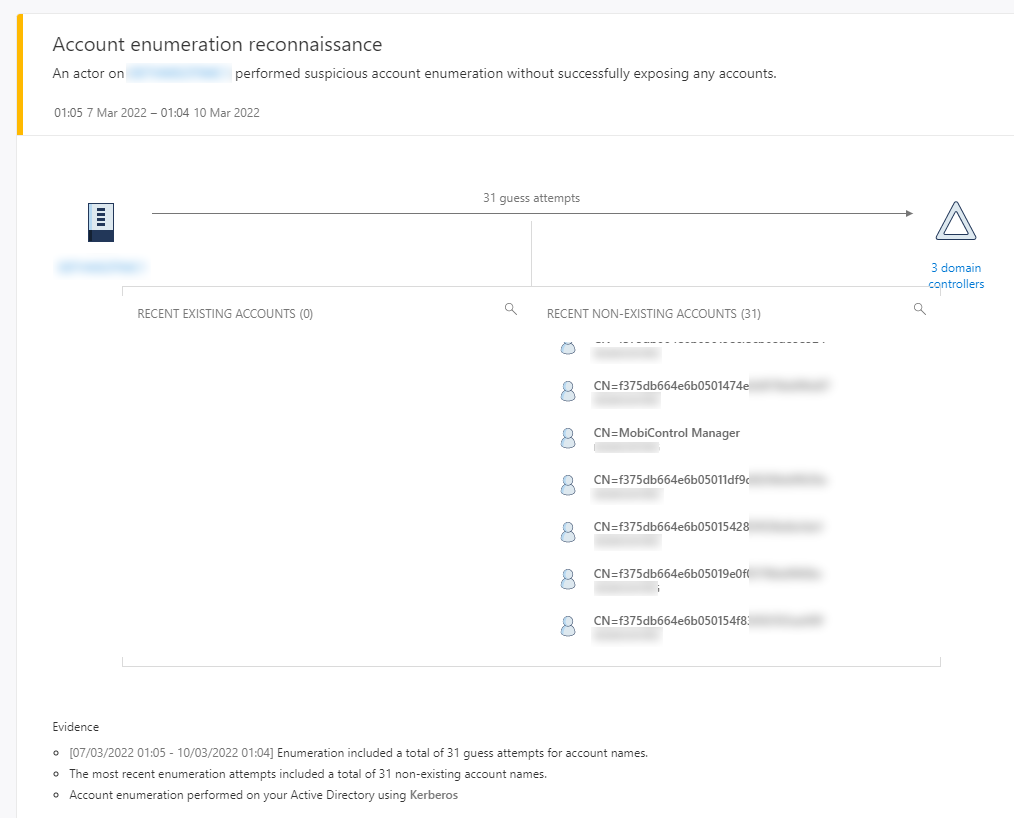
Hi all,
we're using SOTI MobiControl (On-Premise) and saw in some warnings in our Microsoft Defender for Identity Portal.
SOTI MC is doing Kerberos requests against our Domain Controllers using the Device IDs of our Zebra devices:
This is happening every 2 hours when the device agent does a check in.
Is this an configuration issue or a normal behavior? Is there anything we can do in order to stop this?
Best regards,
Patrick